Amazon.com: HackyPi - Ultimate DIY USB Hacking Tool for Security Professionals and Ethical Hackers, DIY Programmable Hacking USB for Educational Purposes : Electronics

Juice Jacking: How Hackers Can Steal Your Info When You Charge Devices - Hashed Out by The SSL Store™

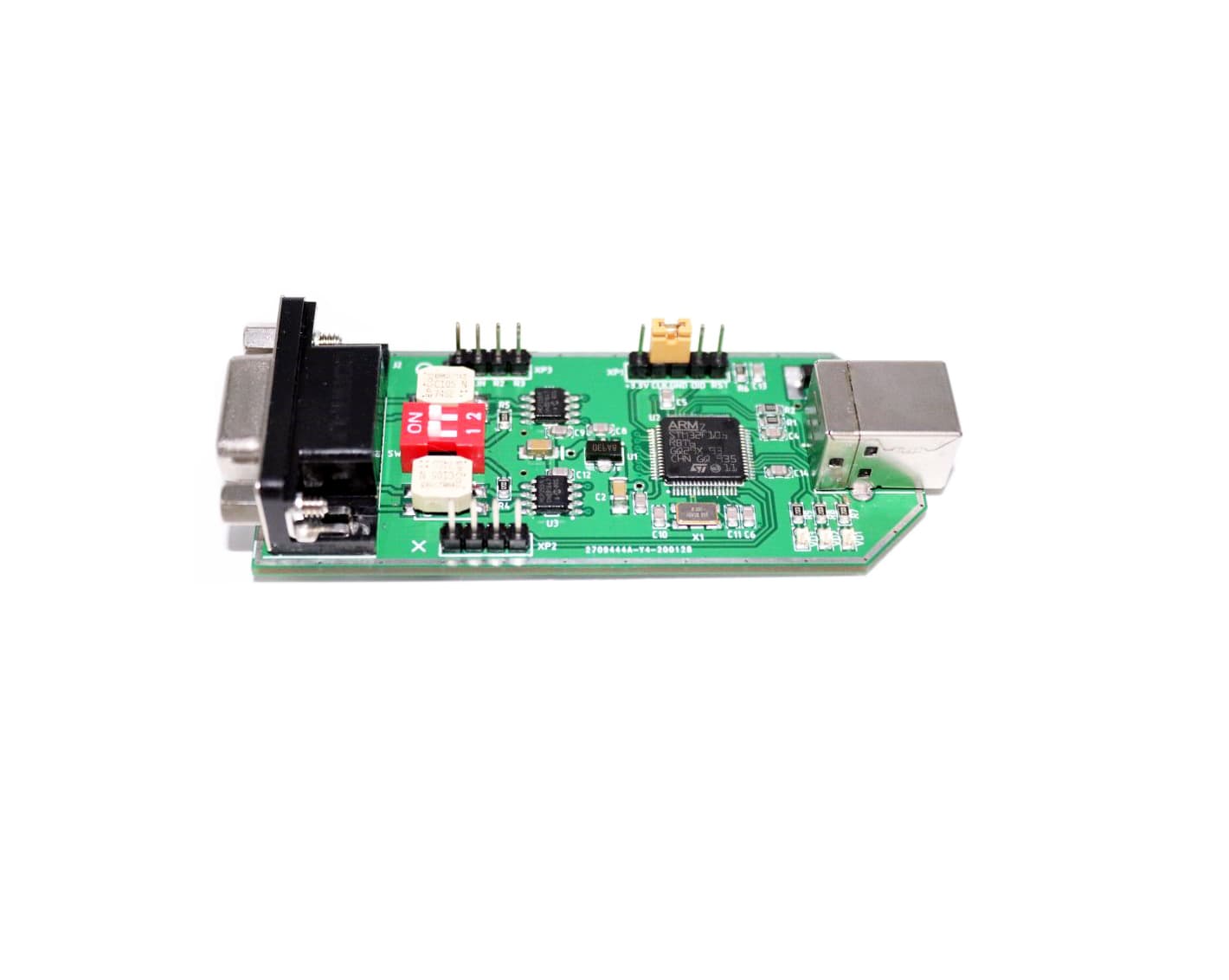
Hacker X-PRO USB-Interface V2 | Programmierhilfen für Brushless-Regler | Regler und externes BEC | Alles für den Elektroflug

O.MG Elite Cable has power of a $20,000 hacking tool; can compromise iPhone, Android, Mac, PC - 9to5Mac

Amazon.com: USB Data Blocker -Protect Against Juice Jacking,Hack Proof 100% Guaranteed, Protection from Illegal Downloading, Any Other USB Device Charging, USB- Data Blocker (2 Red) : Electronics










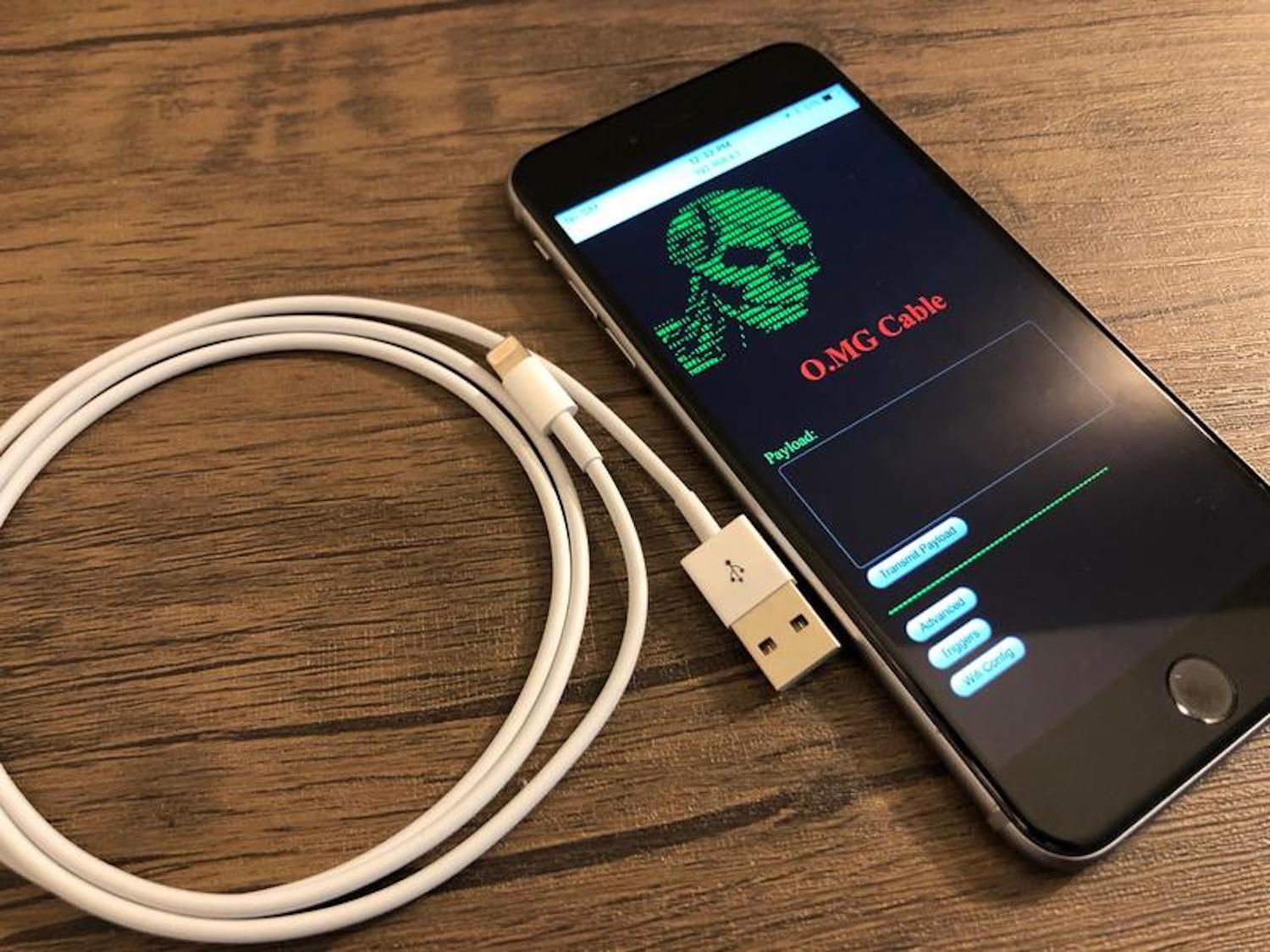
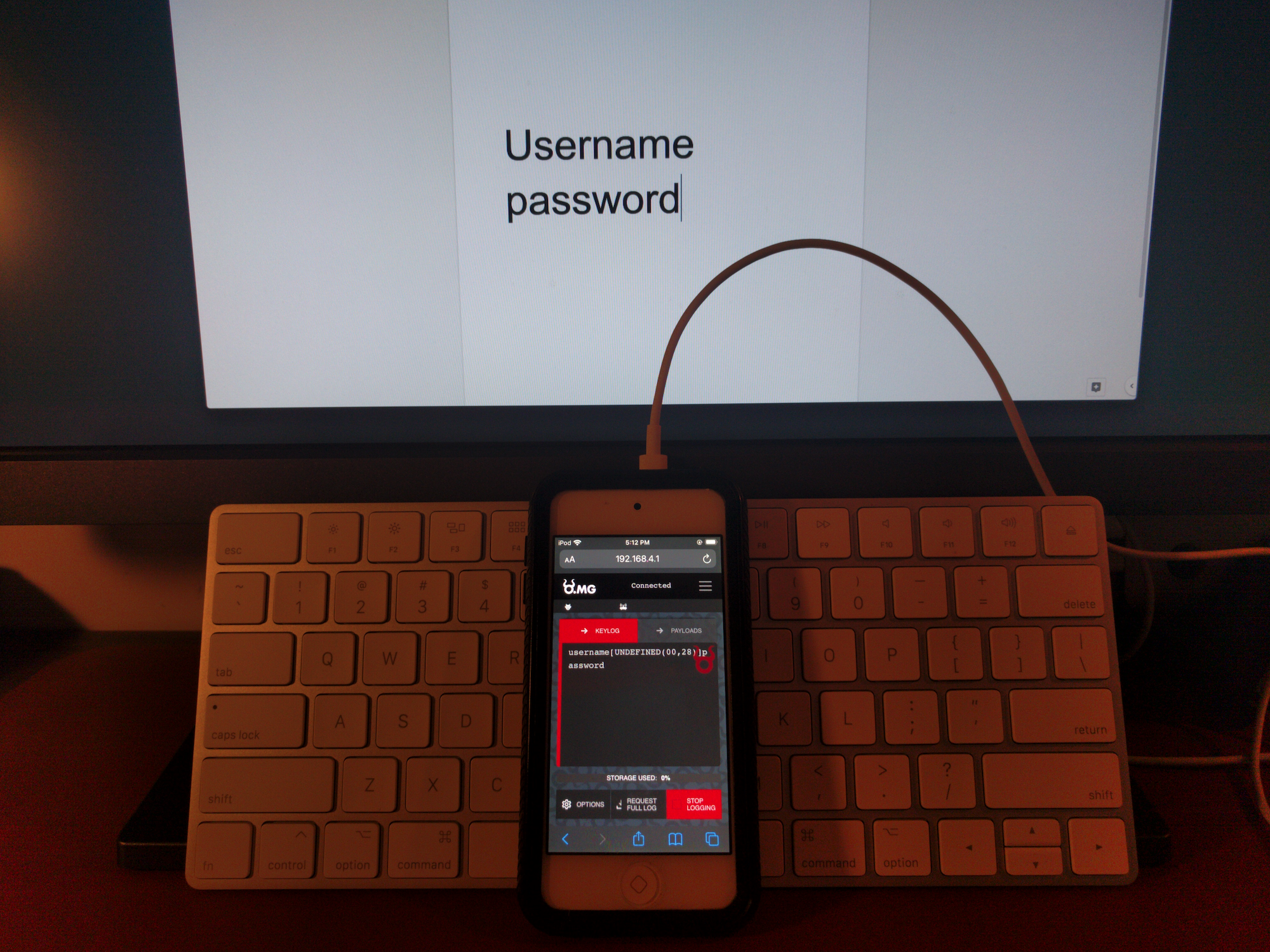

/cdn.vox-cdn.com/uploads/chorus_asset/file/23957231/acastro_226156_omgCable_0001.jpg)